Thick Client Security-Reverse Shell Using DLL Hijacking Vulnerability
In the Below example, i will be explaining how to exploit dll hijacking vulnerability to get reverse shell of a victim machine.
Tools & OS used: Windows 7, Kali linux ,vulnerable application, process monitor(microsoft sysinternals tool).
Pre Conditions to escalate privilege using DLL Hijacking Vulnerability:
Write Permission on a system folder
Software Installation in a non-default directory
A service that is running as a system and is missing a DLL
Permission for restarting the service
Step1: Capture the traffic using Microsoft sysinternals tool “process monitor” and use proper filter while capturing the traffic as shown below.
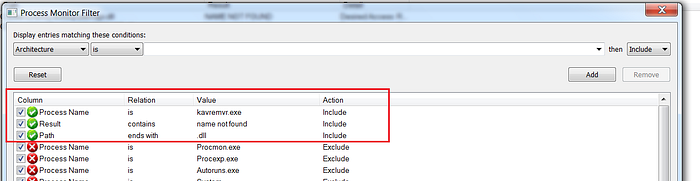
Step2: Open the vulnerable application and look for name not found dll’s belongs to application.
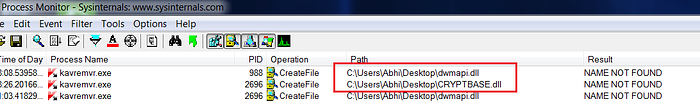
Step3: In the below screenshots one can observe that application is looking for 2 dll’s at desktop location and the dll’s are dwmapi.dll & CRYPTBASE.dll
Step4: Now we need to craft a malicious dll to get reverse shell of a victim machine using msf venom in kali linux. below is the command.
In the below command we need to give kali linux IP and 4444 is a default port, we can use other ports as well.


Step5: Now malicious payload is generated and we can find the payload under home directory.

Step6: Now copy the newly generated malicious dll (inject.dll) to victim machine (windows 7). Rename the malicious dll to dwmapi.dll and save in desktop(desktop is the location where the dll’s are not found).

Step7: Now we need to create a listener in kali linux to receive the input or reverse shell from a victim machine.
Commands to create a tcp listenser can be found in below screenshot.

Step8: Close and restart the application.

Step9: when application calls and executes this malicious dll (dwapi.dll), we will get a reverse shell of victim machine and we can find the victim’s session at tcp listener.

Step10: Now we will enter into victim’s session and navigate to victim’s desktop.

This is how we take the reverse shell of a victim machine using dll hijacking vulnerability.
Mitigations:
1.Digitally sign all the dll’s used in thickclient application using organization certificate.
2.Instead of a relative path use absolute path while loading dll’s.
!! Happy Learning !!
